Turn Global Hacker Talent Into Your Security Advantage with a Bug Bounty Program
Continuous, incentive-driven testing — powered by verified researchers.
Continuous, incentive-driven testing — powered by verified researchers.
A Bug Bounty Program turns hackers into your security partners. You define what systems can be tested, and researchers compete to find vulnerabilities — earning rewards for valid reports. It’s like having hundreds of penetration testers working for you, on demand, around the clock.
With V-Formation, you control the scope, budget, and visibility — while we handle triage, communication, and payouts safely.
Every organization has a different security maturity. That’s why V-Formation lets you tailor your program to your exact requirements — from small private tests to full open challenges.
Choose what you want to protect:
• Web applications
• APIs & microservices
• LLM agents
• Cloud environments
• Critical infrastructure or internal assets
Choose how you want to run it:
• Private programs
• Public programs
• Hybrid models
We build the program around your goals — not the other way around.
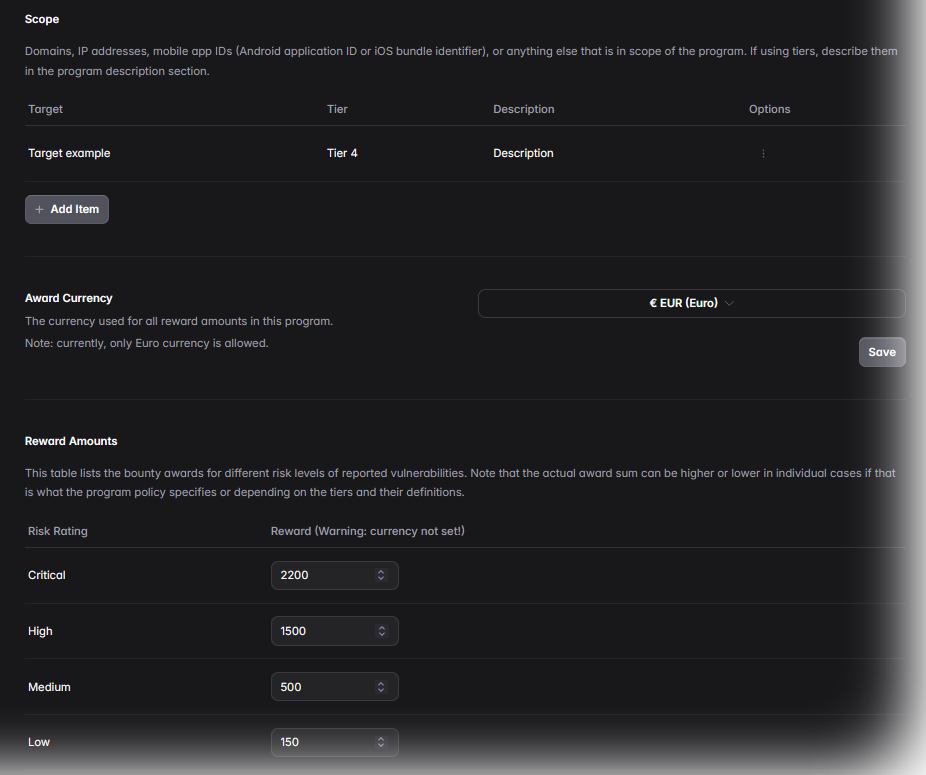
Most pentests happen once or twice a year. But vulnerabilities appear with every new deployment, API, or feature. Bug bounties offer continuous testing — 24/7 coverage that evolves with your product.
Bug bounty researchers think like attackers — not auditors. They uncover creative, chained, and high-impact vulnerabilities that automated scanners and traditional tests often miss.
Instead of paying for time, you pay for results. Rewards are only issued for validated vulnerabilities — making it one of the most cost-efficient security investments possible.
The best researchers aren’t on your payroll. Through V-Formation, you tap into a trusted, verified community of cybersecurity experts — with diverse skills across web, cloud, API, and mobile targets.
Bug bounties scale effortlessly as your digital footprint grows. You can launch private programs for limited testing or open programs for large-scale coverage — without expanding your internal security team.
V-Formation integrates your bug bounty workflow into existing CI/CD and incident management processes — providing continuous insights and measurable improvement metrics.
With V-Formation, you don’t pay for hours spent — you pay for results.
This means:
✔ No paying for “time on task”
✔ No expensive consulting packages
✔ No hidden fees
✔ No rewards for invalid reports
You pay only for vulnerabilities that are:
• reproducible
• validated
• impactful
• triaged by experts
V-Formation delivers crowd-powered security without budget surprises.
Whether you’re launching your first VDP or scaling a global bug bounty, our managed programs adapt to your workflow.
No rigid packages — only configurations that fit your organization’s risk profile, size, and internal capacity.
We cultivate a trusted network of ethical hackers across the globe.
This means culturally aligned collaboration, faster communication, and high-quality findings in multiple languages.
Our pricing model is simple and fair — no hidden fees, no inflated rewards.
You pay for validated impact, not bureaucracy.
V-Formation was built by hackers, threat hunters, and cyber security experts — not marketers.
We understand your challenges because we’ve lived them. That’s why our platform focuses on actionable results, not vanity metrics.